Intuitive Identification for Seamless Access.
Intuitive Identification for Seamless Access.
Intuitive Identification for Seamless Access.
Create trust at onboarding and beyond with a complete, AI-powered digital identity solution built to help you know your customers online.
Create trust at onboarding and beyond with a complete, AI-powered digital identity solution built to help you know your customers online.
Create trust at onboarding and beyond with a complete, AI-powered digital identity solution built to help you know your customers online.







Explore Features
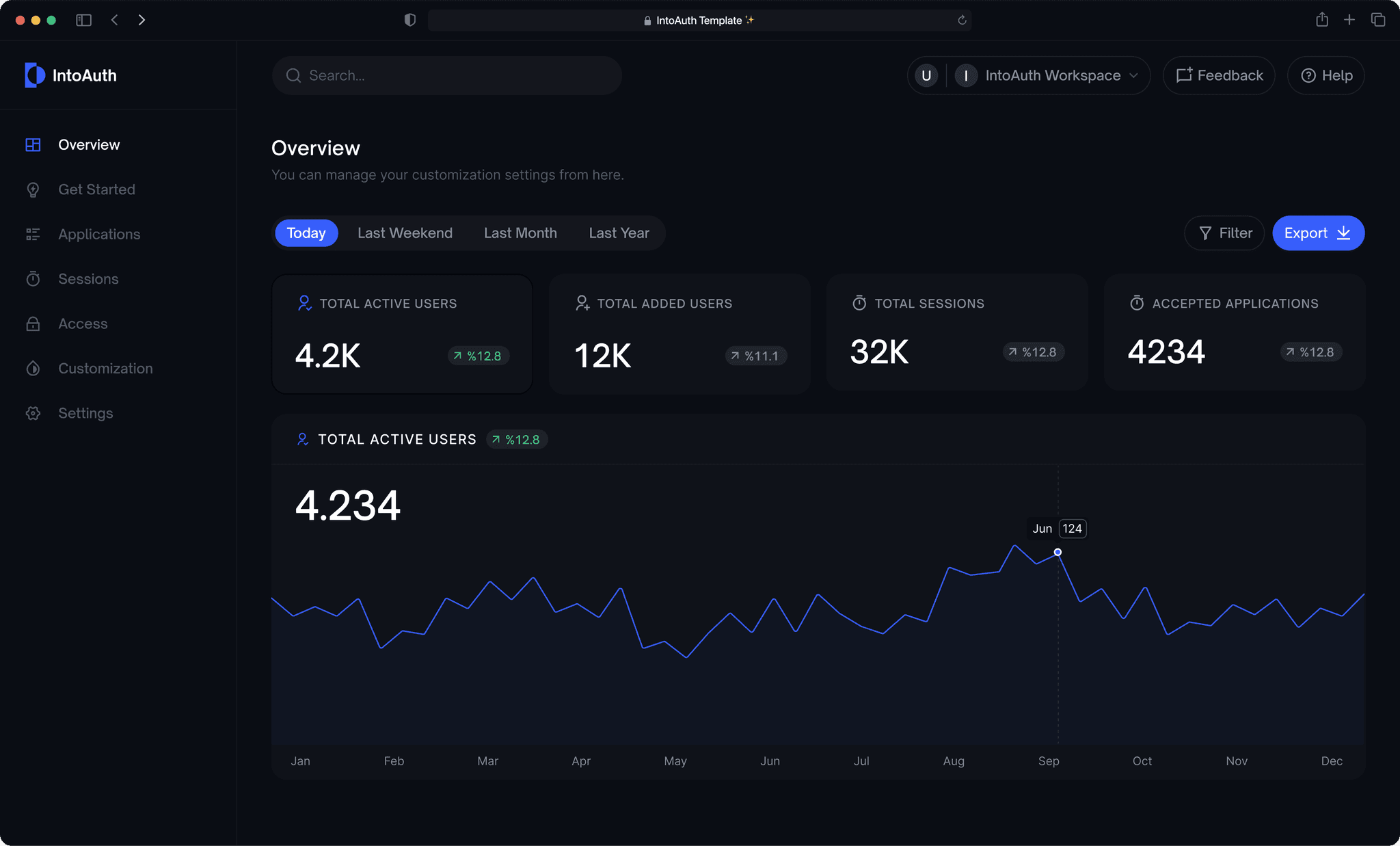
Innovative Features
Groundbreaking capabilities that elevate your journey and drive remarkable results.

Real-Time Threat Analytics
Utilize advanced analytics and machine learning for real-time detection and response to security breaches or suspicious activities.

Biometric Authentication Options
Enhance security with fingerprint, facial recognition, or iris scanning, adding an extra layer of protection against unauthorized...

Adaptive Multi-Factor Authentication
Add security layers with context-aware and risk-based authentication, ensuring seamless user experience across varying risk levels.

Real-Time Threat Analytics
Enhance security with fingerprint, facial recognition, or iris scanning, adding an extra layer of protection against unauthorized...

Customizable UI
Efficiently manage user lifecycles with centralized provisioning and de-provisioning across all systems and apps.

Automated Access Governance
Continuously monitor and enforce access policies to maintain compliance with industry regulations and internal security protocols.

Explore Features
Innovative Features
Groundbreaking capabilities that elevate your journey and drive remarkable results.

Real-Time Threat Analytics
Utilize advanced analytics and machine learning for real-time detection and response to security breaches or suspicious activities.

Biometric Authentication Options
Enhance security with fingerprint, facial recognition, or iris scanning, adding an extra layer of protection against unauthorized...

Adaptive Multi-Factor Authentication
Add security layers with context-aware and risk-based authentication, ensuring seamless user experience across varying risk levels.

Real-Time Threat Analytics
Enhance security with fingerprint, facial recognition, or iris scanning, adding an extra layer of protection against unauthorized...

Customizable UI
Efficiently manage user lifecycles with centralized provisioning and de-provisioning across all systems and apps.

Automated Access Governance
Continuously monitor and enforce access policies to maintain compliance with industry regulations and internal security protocols.

Explore Features
Innovative Features
Groundbreaking capabilities that elevate your journey and drive remarkable results.

Real-Time Threat Analytics
Utilize advanced analytics and machine learning for real-time detection and response to security breaches or suspicious activities.

Biometric Authentication Options
Enhance security with fingerprint, facial recognition, or iris scanning, adding an extra layer of protection against unauthorized...

Adaptive Multi-Factor Authentication
Add security layers with context-aware and risk-based authentication, ensuring seamless user experience across varying risk levels.

Real-Time Threat Analytics
Enhance security with fingerprint, facial recognition, or iris scanning, adding an extra layer of protection against unauthorized...

Customizable UI
Efficiently manage user lifecycles with centralized provisioning and de-provisioning across all systems and apps.

Automated Access Governance
Continuously monitor and enforce access policies to maintain compliance with industry regulations and internal security protocols.


Inovative Features
Flagship Functionalities
Groundbreaking capabilities that elevate your journey and drive remarkable results.
Identity Access Management
Centralized user provisioning, de-provisioning, and access management across various applications and systems, ensuring efficient and consistent access control.

Multi-Factor Authentication
Fortify security with our adaptive Multi-Factor Authentication, implementing additional verification factors based on real-time risk analysis for enhanced protection.

Customizable UI Screens
Seamlessly integrate your brand's identity into every login touchpoint with our flexible Ul customization. From color palettes to typography, tailor each element to craft.

Inovative Features
Flagship Functionalities
Groundbreaking capabilities that elevate your journey and drive remarkable results.

Identity Access Management
Centralized user provisioning, de-provisioning, and access management across various applications and systems, ensuring efficient and consistent access control.

Multi-Factor Authentication
Fortify security with our adaptive Multi-Factor Authentication, implementing additional verification factors based on real-time risk analysis for enhanced protection.

Customizable UI Screens
Seamlessly integrate your brand's identity into every login touchpoint with our flexible Ul customization. From color palettes to typography, tailor each element to craft.

Inovative Features
Flagship Functionalities
Groundbreaking capabilities that elevate your journey and drive remarkable results.

Identity Access Management
Centralized user provisioning, de-provisioning, and access management across various applications and systems, ensuring efficient and consistent access control.

Multi-Factor Authentication
Fortify security with our adaptive Multi-Factor Authentication, implementing additional verification factors based on real-time risk analysis for enhanced protection.

Customizable UI Screens
Seamlessly integrate your brand's identity into every login touchpoint with our flexible Ul customization. From color palettes to typography, tailor each element to craft.



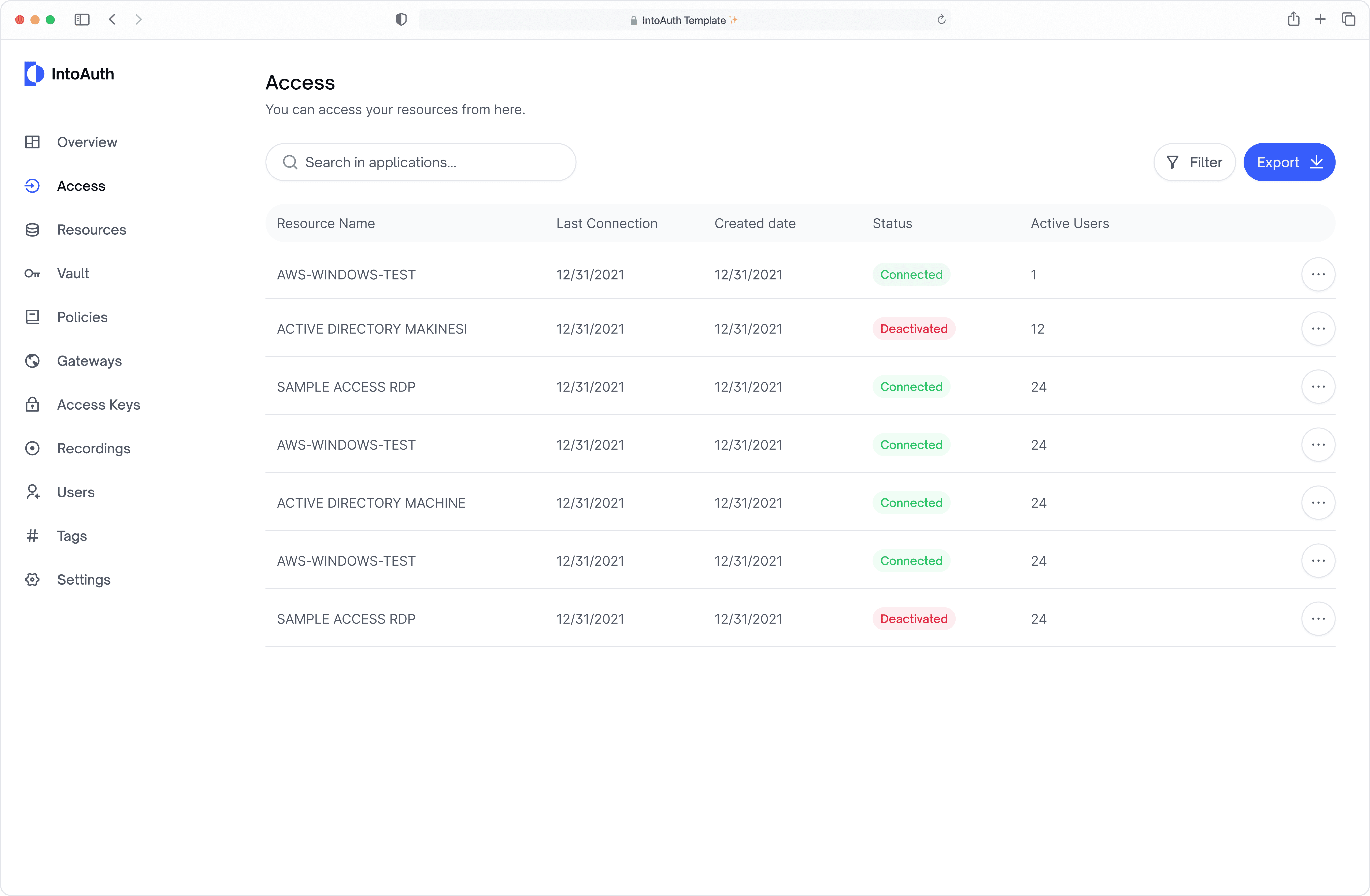
SINGLE-SIGN ON
Single-Sign On Technology
Explore the fundamental principles and best practices of privileged access management (PAM), a crucial security measure for protecting highly privileged accounts and mitigating the risks.

ACCESS RESOURCESS
Privileged Access Management
Streamline access with Single Sign-On, enabling users to securely authenticate once and seamlessly access multiple applications and services without redundant logins.


SINGLE-SIGN ON
Single-Sign On Technology
Explore the fundamental principles and best practices of privileged access management, a crucial security measure for protecting highly privileged accounts and mitigating.


ACCESS RESOURCESS
Privileged Access Management
Streamline access with Single Sign-On, enabling users to securely authenticate once and seamlessly access multiple applications and services without redundant logins.


SINGLE-SIGN ON
Single-Sign On Technology
Explore the fundamental principles and best practices of privileged access management (PAM), a crucial security measure for protecting highly privileged accounts and mitigating the risks.


ACCESS RESOURCESS
Privileged Access Management
Streamline access with Single Sign-On, enabling users to securely authenticate once and seamlessly access multiple applications and services without redundant logins.


Customizable Login Screens
Tailored Login Touchpoints
Thoughtfully design access experiences that authentically embody your brand's unique persona, core values, and vision, fostering meaningful...
Overpass
Inter
Playfair Display

Customizable Login Screens
Tailored Login Touchpoints
Thoughtfully design access experiences that authentically embody your brand's unique persona, core values, and vision, fostering meaningful...

Customizable Login Screens
Tailored Login Touchpoints
Thoughtfully design access experiences that authentically embody your brand's unique persona, core values, and vision, fostering meaningful...


Pricing
Unlocking Value Pricing Plans Options
Explore our flexible pricing options tailored to your needs, ensuring affordability and scalability for every stage of your authentication journey.
Monthly
Yearly
Starts at
$50
/ Monthly
Starter Package
Essential authentication tools for small businesses.

Single Sign-On (SSO) Integration

MFA, OTP and Push Customization

Customizable Login Interfaces

User Provisioning/De-Provisioning

24/7 Live Support
Starts at
$150
/ Monthly
Professional Package
Risk-based MFA, biometrics, access governance, threat monitoring.

All Features from Starter Package

Adaptive Risk-Based Authentication

Authentications (Fingerprint, Face ID)

Real-Time Threat Monitoring

Single Sign-On (SSO) Integration
Most Popular
Starts at
$350
/ Monthly
Enterprise Package
PAM, continuous authentication, FIDO2, on-prem deployment.

All Features from Professional Package

Privileged Access Management (PAM)

Advanced Threat Analytics

Dedicated Customer Success Manager

FIDO2 & WebAuthn Support

Pricing
Unlocking Value Pricing Plans Options
Explore our flexible pricing options tailored to your needs, ensuring affordability and scalability for every stage of your authentication journey.
Monthly
Yearly
Starts at
$50
/ Monthly
Starter Package
Essential authentication tools for small businesses.

Single Sign-On (SSO) Integration

MFA, OTP and Push Customization

Customizable Login Interfaces

User Provisioning/De-Provisioning

24/7 Live Support
Starts at
$150
/ Monthly
Professional Package
Risk-based MFA, biometrics, access governance, threat monitoring.

All Features from Starter Package

Adaptive Risk-Based Authentication

Authentications (Fingerprint, Face ID)

Real-Time Threat Monitoring

Single Sign-On (SSO) Integration
Most Popular
Starts at
$350
/ Monthly
Enterprise Package
PAM, continuous authentication, FIDO2, on-prem deployment.

All Features from Professional Package

Privileged Access Management (PAM)

Advanced Threat Analytics

Dedicated Customer Success Manager

FIDO2 & WebAuthn Support

Pricing
Unlocking Value Pricing Plans Options
Explore our flexible pricing options tailored to your needs, ensuring affordability and scalability for every stage of your authentication journey.
Starts at
$50
/ Yearly
Starter Package
Essential authentication tools for small businesses.

Single Sign-On (SSO) Integration

MFA, OTP and Push Customization

Customizable Login Interfaces

User Provisioning/De-Provisioning

24/7 Live Support
Starts at
$150
/ Yearly
Professional Package
Risk-based MFA, biometrics, access governance, threat monitoring.

All Features from Starter Package

Adaptive Risk-Based Authentication

Authentications (Fingerprint, Face ID)

Real-Time Threat Monitoring

Single Sign-On (SSO) Integration
Most Popular
Starts at
$350
/ Yearly
Enterprise Package
PAM, continuous authentication, FIDO2, on-prem deployment.

All Features from Professional Package

Privileged Access Management (PAM)

Advanced Threat Analytics

Dedicated Customer Success Manager

FIDO2 & WebAuthn Support
Monthly
Yearly


User Stories
Clients Endorse Our Authentication Capabilities
Clients Endorse Our Authentication Capabilities
Invite visitors to uncover the endless possibilities and opportunities that your product/service opens up for them.
Invite visitors to uncover the endless possibilities and opportunities that your product/service opens up for them.

Umutcan Eyriyer
Designer
IntoAuth's adaptive authentication platform has transformed our security landscape, providing unparalleled protection while ensuring a frictionless user experience...

Yusuf Kaan Usta
Framer Developer
"With IntoAuth's comprehensive suite of authentication solutions, we've been able to streamline access governance, mitigate risks, and maintain compliance with ease."

Oğuz Yağız Kara
Founder & Designer
"The level of customization and branding capabilities offered by IntoAuth's login interfaces has allowed us to create truly immersive and on-brand...

Mert Can Eyriyer
Product Designer
"IntoAuth's privileged access management capabilities streamlined governance over critical accounts, mitigating insider threats and ensuring compliance."

Umutcan Eyriyer
Designer
IntoAuth's adaptive authentication platform has transformed our security landscape, providing unparalleled protection while ensuring a frictionless user experience...

Yusuf Kaan Usta
Framer Developer
"With IntoAuth's comprehensive suite of authentication solutions, we've been able to streamline access governance, mitigate risks, and maintain compliance with ease."

Oğuz Yağız Kara
Founder & Designer
"The level of customization and branding capabilities offered by IntoAuth's login interfaces has allowed us to create truly immersive and on-brand...

Mert Can Eyriyer
Product Designer
"IntoAuth's privileged access management capabilities streamlined governance over critical accounts, mitigating insider threats and ensuring compliance."

Umutcan Eyriyer
Designer
IntoAuth's adaptive authentication platform has transformed our security landscape, providing unparalleled protection while ensuring a frictionless user experience...

Yusuf Kaan Usta
Framer Developer
"With IntoAuth's comprehensive suite of authentication solutions, we've been able to streamline access governance, mitigate risks, and maintain compliance with ease."

Oğuz Yağız Kara
Founder & Designer
"The level of customization and branding capabilities offered by IntoAuth's login interfaces has allowed us to create truly immersive and on-brand...

Mert Can Eyriyer
Product Designer
"IntoAuth's privileged access management capabilities streamlined governance over critical accounts, mitigating insider threats and ensuring compliance."



Frequently Asked Questions
Everything you need to know.

What is Identity Management?
What is multi-factor authentication (MFA) and how does it work?
What are the different types of MFA factors (e.g. biometrics, OTP...
How does risk-based authentication enhance security?
How does identity management improve security and compliance?
Can you explain the process of user provisioning and deprovisioni...


Frequently Asked Questions
Everything you need to know.

What is Identity Management?
What is multi-factor authentication (MFA) and how does it work?
What are the different types of MFA factors (e.g. biometrics, OTP...
How does risk-based authentication enhance security?
How does identity management improve security and compliance?
Can you explain the process of user provisioning and deprovisioni...


Frequently Asked Questions
Everything you need to know.

What is Identity Management?
What is multi-factor authentication (MFA) and how does it work?
What are the different types of MFA factors (e.g. biometrics, OTP...
How does risk-based authentication enhance security?
How does identity management improve security and compliance?
Can you explain the process of user provisioning and deprovisioni...



Popular Articles
Recommended Readings
Discover our editors meticulously curated collection of thought provoking longform articles.

Popular Articles
Recommended Readings
Discover our editors meticulously curated collection of thought provoking longform articles.

Popular Articles
Recommended Readings
Discover our editors meticulously curated collection of thought provoking longform articles.
Join Today
Explore IAM, MFA, PAM.












